Jenkins contains sensitive information. Thus it must be secured, like any other sensitive platform. Thankfully Jenkins provides you with many security options. This guide will show you all the essential bits that you need to know.
You access these features on the Configure Global Security page under manage Jenkins.
Let’s look at some of the security features:
Table of Contents
Authentication
This feature allows you to disable the Jenkins “Remember Me Cookie” for added security.
Security Realm
Jenkins supports many different authentication systems through security realms. A security realm tells Jenkins which authentication source to use. Thus, the security realm contains the user information for authentication.
- Delegate to a servlet container. Thus a servlet container running something like Jetty will do the authentication.
- Jenkins’ user database. As the name suggests, this delegates authentication to the Jenkins database.
- LDAP – this delegates authentication to a configured LDAP server. In this case, LDAP will control both users and groups.
- Unix user/group database. This delegates authentication to the Jenkins controller’s underlying Unix OS-level user database.
Authorization
Authorization indicates what an authenticated user can access in the Jenkins environment. These are the supported options:
- Anyone can do anything – Everyone gets complete control of Jenkins. This setting includes anonymous users who haven’t logged in.
- Legacy mode – Legacy mode behaves the same as Jenkins <1.164.
- Logged-in users can do anything – Every logged-in user gets complete control of Jenkins.
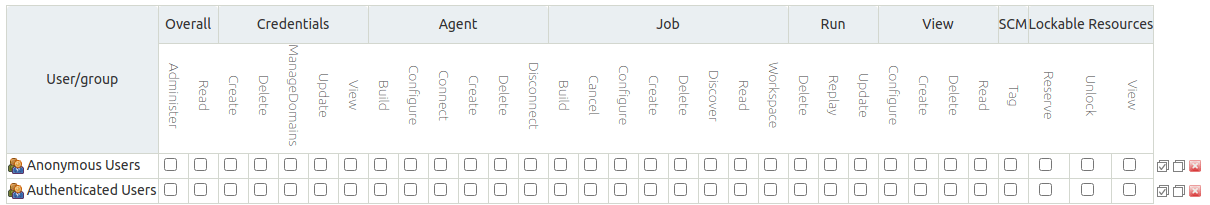
- Matrix-based security – This authorization scheme allows for granular control. So you can decide what users and groups can perform. (see screenshot below)
- Project-based Matrix Authorization Strategy – This scheme is an extension to Matrix-based security. But this scheme allows project-based access control lists (ACLs). So, for example, you can define security on a project level instead of all projects.
Markup Formatter
The following Jenkins security setting is Markup Formatting. We recommend that you set this to plain text will eliminate any unsafe HTML or JavaScript.
Agents
Jenkins uses Agents to distribute work. As such, Jenkins uses the JNLP TCP port to communicate with the Agents. JNLP stands for Java Network Launch Protocol, in case you did not know. You can disable this port if you do not have a distributed system. But, enable it if needed by selecting either a fixed port or a random port. The fixed port value is typically 50000.
CSRF Protection
CSRF (Cross-Site Request Forgery) is a type of security vulnerability in web applications. Thankfully you can protect Jenkins by enabling CSRF protection.
This Jenkins security feature does this by placing a crumb that it can later use to validate requests. Generally, requests sent using the POST method are subject to CSRF protection.
The crumb contains information identifying the user, such as:
- The user name
- A salt unique to this Jenkins instance
- The web session ID
- The IP address
You can also enable proxy compatibility for CSRF crumbs. Enabling proxy compatibility removes information about the user’s IP address from the token.
A failed CSRF error would look something like this:
HTTP ERROR 403 No valid crumb was included in the request
URI: /createItem
STATUS: 403
MESSAGE: No valid crumb was included in the request
SERVLET: StaplerAgent to controller security
Then next, we will look at the “Agent to Controller Security” setting. This Jenkins security setting prevents agent processes from sending malicious commands to the Jenkins controller.
Wrapping up
In conclusion, this guide has shown you how to do some of the basic security configurations within Jenkins.


